Realm
Realm is a red team engagement tool that I have joined onto! This project, a collobration between me and other colleagues, is meant to focus on automation in the red team process. With a full interpreting language customized to red team functions, the agents are able to work very efficiently.
Sombra
As a member of the RITSEC Red Team, I developed a tool to use to compete in the many competitons we go to. My tool, named RShell, is an ICMP shell using raw sockets. It uses specific data tagged to the end of ICMP packets to indicate their command, and then the client sends an ICMP packet back to the server with the result. The interface used by the server is an ncurses TUI that gives you a variety of options for mass-sending commands and viewing your results!
Blue Team Defense Tools
To create a larger variety of fast tools to automate a large quantity of my common Linux defense tasks, I developed a suite of various Python scripts to assist in Blue Team defense for Red vs Blue Competitions. I used my experience from classwork and competiting at University of Buffalo Lockdown to identify what was the most common attack methods and how I can automate my defense against them. Some of its features incluide automated auditing of accounts, configurations, and permissions to remove the low-hanging fruit. Furthermore, based off of my work on RustyBlue (See Below), I use network monitoring and process tracking to detect and eliminate reverse shells and similar malware.

RustyBlue
Looking to write more code in low-level languages and with cybersecurity competitions in mind, I chose to dive into Rust for this project. I have lately taken interest to netwoork analysis and monitoring, so I thought I would write something to help me during Blue Team competitions in Rust. Hence, RustyBlue was born! As of now, the project serves two functions. It has "sniff" mode, which essentially runs as Wireshark in the terminal. There is also "anomaly" mode, which follows a given YAML file to tell what data is safe and what may be an attacker. This was very fun to write since I had to manually parse the entire network packet layer by layer. The PCAP library provides each packet's data as an array of 8-bit integer values, so I then had to research the headers of each layer and protocol to ensure it is properly parsed and displayed.

Red Team Recruiting
As part of the RITSEC Red Team Recruiting group, all members were tasked with creaeting a C2 (Command and Control) system. These consisted of a server software that would manage connections and send commands out to the clients, and client software to establish connections and execute any given command. Mine, written in python, was capable of executing shell commands and file upload/download. Alongside this, I wanted to find a fun way to interact with it that wasn't the command line. So, I made the command interface through a Skype chat! Each client gets its own "chat room" with the control account, with a large chat available to execute the same command on all clients.
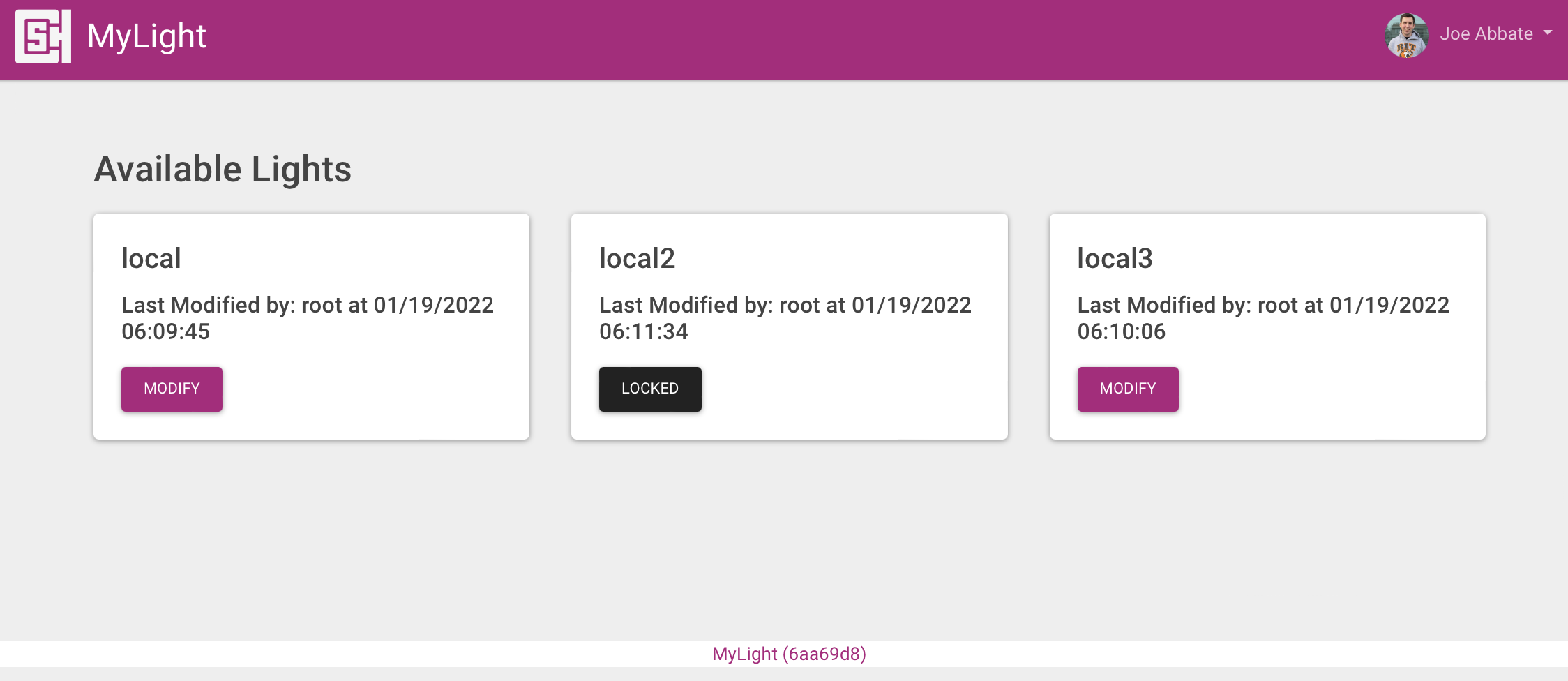
Light
Everyone loves LEDs, right? But who likes getting up to get the remote to change them? This was the dilemma I faced in the Lounge at Computer Science House. In standard computer-geek fashion, I chose to fix it with a webiste. This project uses a Raspberry Pi, Flask Website, and WebSockets to control WS28xx lights. The website is hosted on an OKD cluster, and uses the websockets to control the Pis running a systemd service to run the lights. The proof of concept was done with 3 feet of lights, and I hope to add it to the actual lounge in much larger scale soon!
OpenCV Traffic Light Research
In my Junior Year of High School, I was enrolled in the AP Capstone program and was tasked with a year-long research study on the topic of my choice. Wanting to further my skills in programming, I conducted research on different methods to complete traffic light state identification. Using Java and the OpenCV library to complete the task, this project was my first large code project that wasn't robotics related. This project also forced me to learn how to explain my complex ideas and algorithms in a way that normal people can understand. This project concluded with a 5000 word paper and a fifteen minute presentation on my findings.
